Despite everything going on in the world, there’s been no slowdown in cyberattacks. The increase in the complexity and sophistication of cyberattacks continues to plague cybersecurity experts.
Cybercriminals have found many different ways to enter companies' systems. One of their biggest targets is board directors and executives and one of their easiest ways to gain entrance is through their emails.
Board members get emails asking them for tax information or requesting bank transfers.
It can be difficult to distinguish fraudulent requests like this from real requests
How to protect yourself?
- NEVER EVER give anyone your password. Doesn’t matter who asks or why.
- Avoid opening unsolicited attachments. Scammers use them to transfer malware or viruses.
- Be wary of social engineering. Scammers scrape personal information from the Internet and use it to impersonate friends or authority figures.
- Don’t blindly click links. Hover over the link with your mouse and verify that the link matches the text.
- If you do click an unsolicited link, and it takes you to a sign-in page, DON’T sign in.
- If it sounds too good to be true, it probably is.
Here are some phishing email examples:
Example #1:
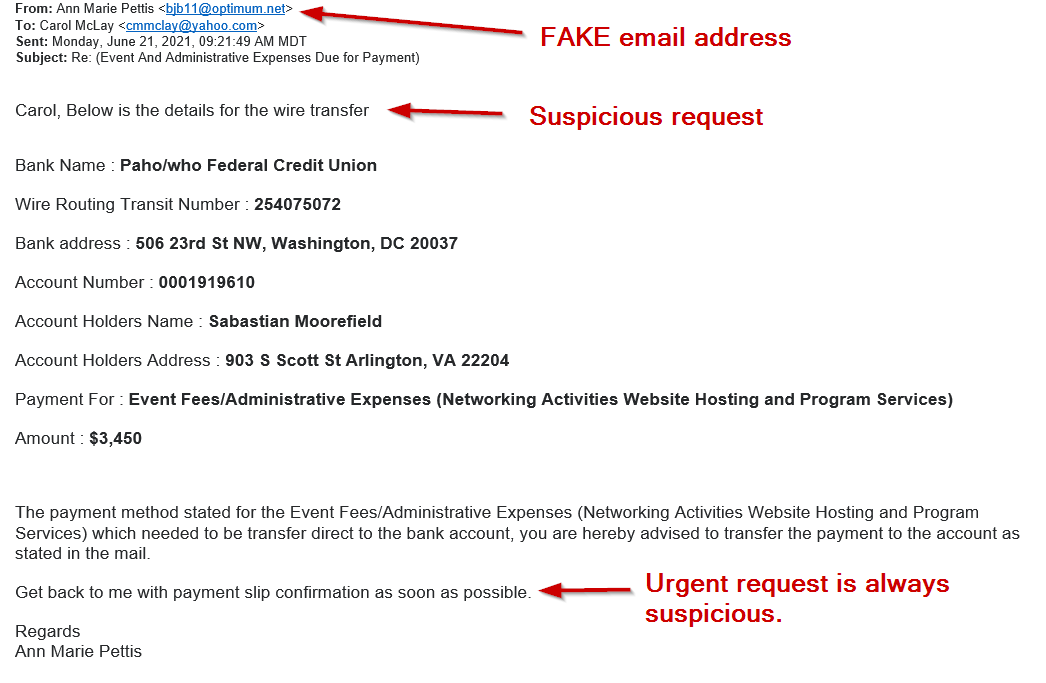
Example #2:
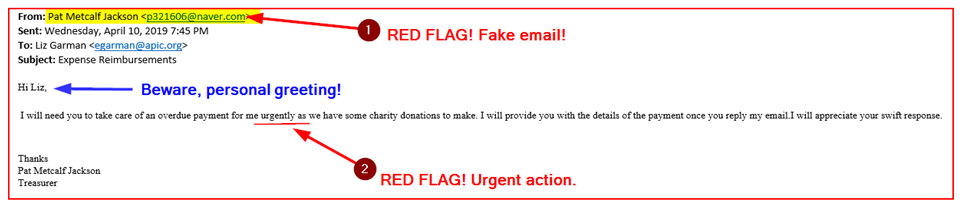
Example #3:
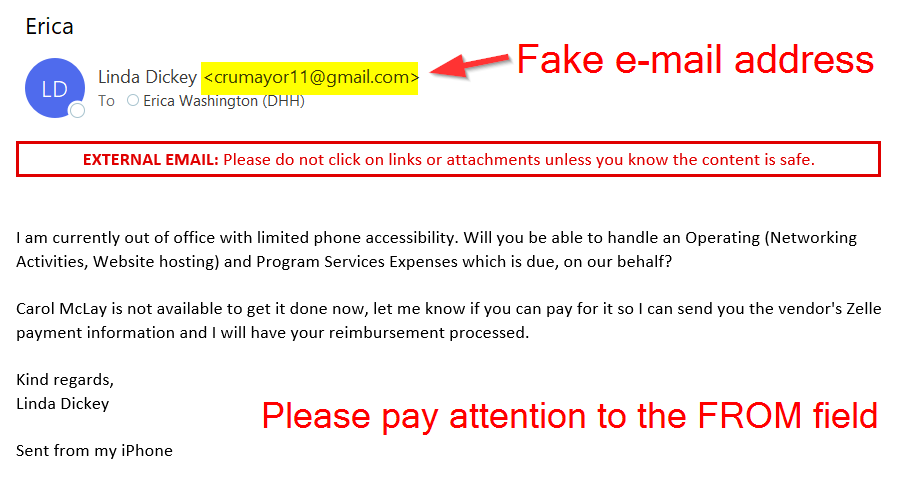
Signs you may have received a phishing email. If one of these is TRUE, it is most likely a SCAM!
- Unofficial “From” address. Look out for a sender’s email address that is similar to, but not the same.
- Urgent action required. Fraudsters often try to get you to react immediately to an email message.
- Nameless greetings. Fraudsters often send bulk emails based on an email list they acquired or purchased.
- Link to a fake website. To trick you into disclosing your username and password, fraudsters often include a link to a fake website.
Unsure if it's a SCAM/Phishing attempt?
If you are unsure whether or not a message you receive is a scam/phishing attempt, send the suspected message with full headers to helpdesk@apic.org. Better to ask before you act.
Be safe!

Comments
0 comments
Please sign in to leave a comment.